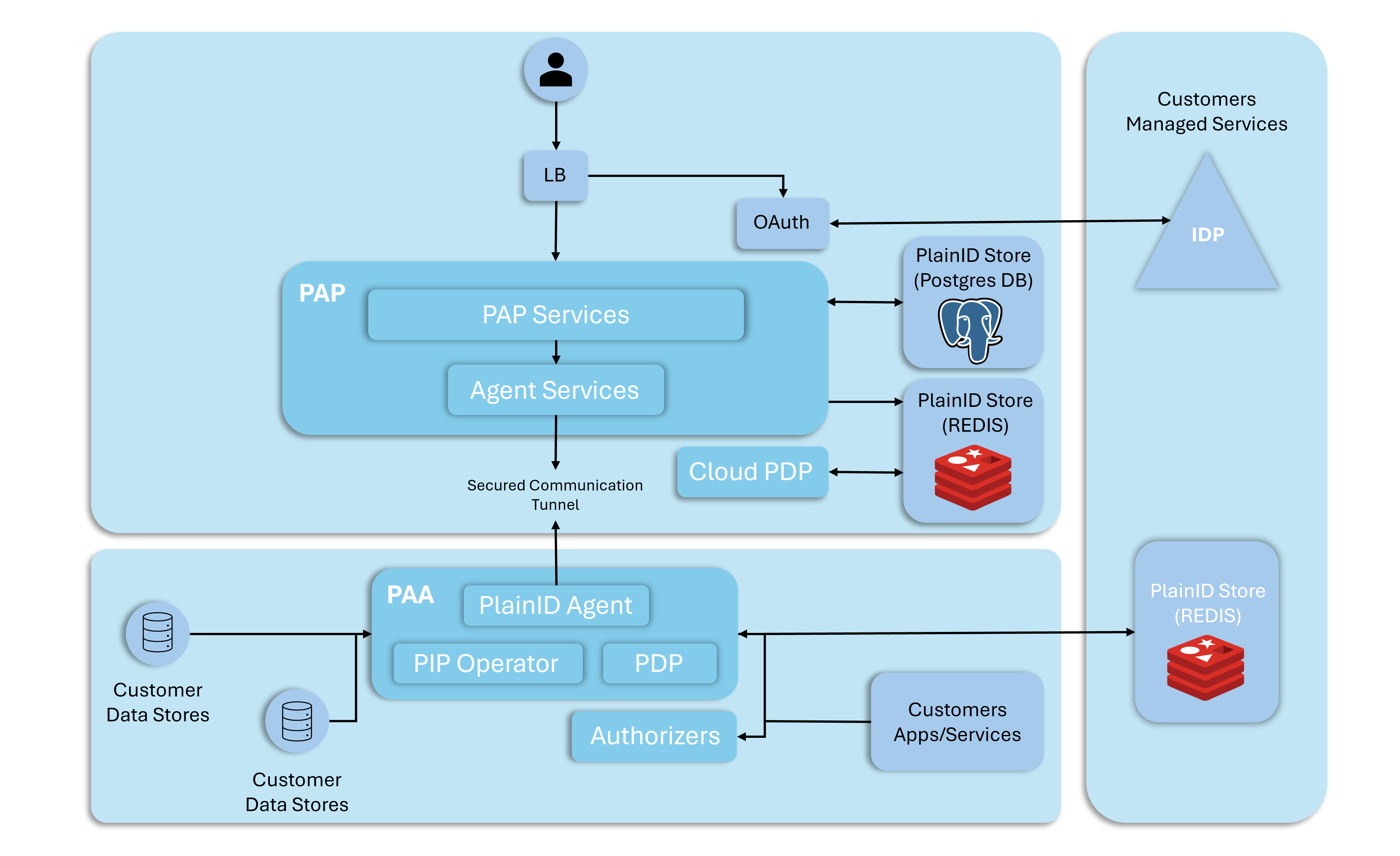
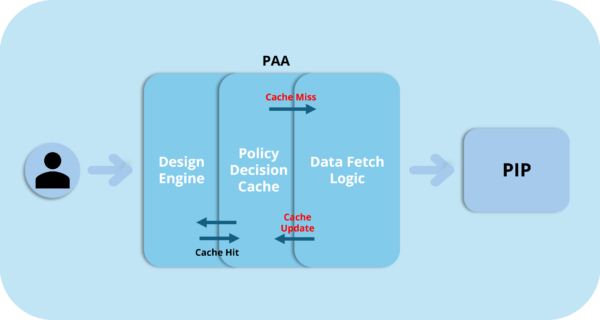
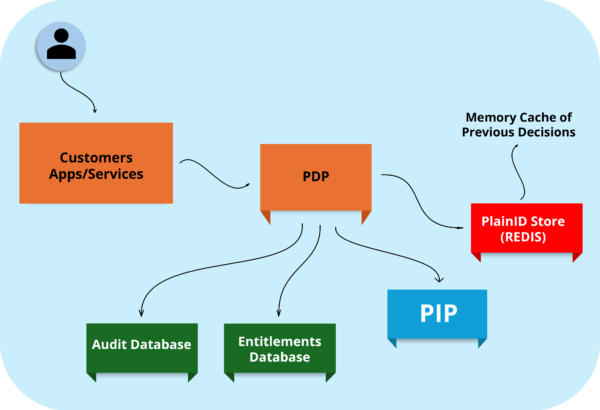
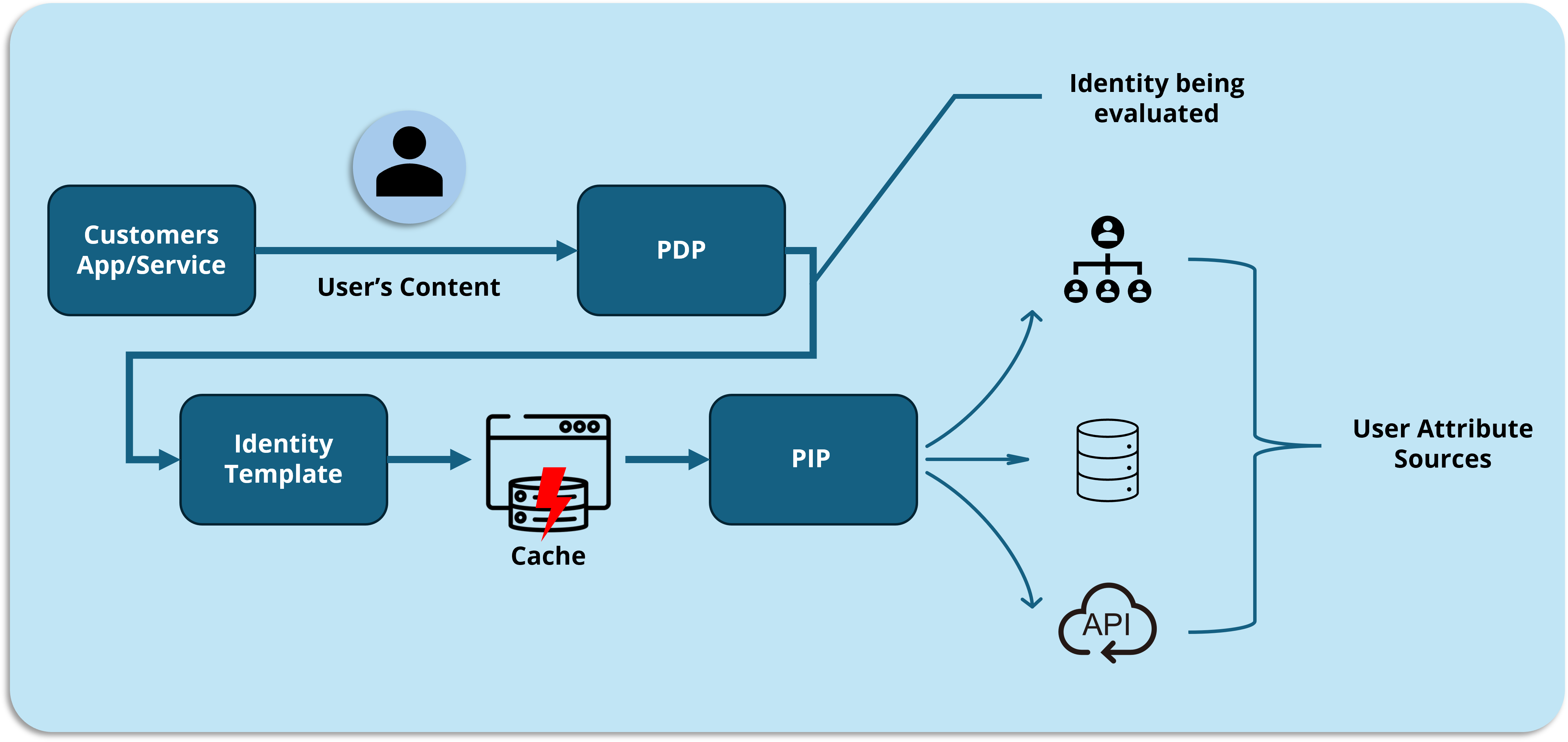
How AI is Revolutionizing Identity Governance
The Identity Crisis in Modern Enterprises
Imagine managing thousands of digital identities across hundreds of applications while ensuring the right people have exactly the right access at the right time—no more, no less. Now imagine doing that manually with spreadsheets and emails in today’s dynamic business environment.
This nightmare scenario is reality for many security teams and identity administrators. With the average large company deploying over 660 SaaS apps, traditional identity governance has hit a breaking point. The consequences? Access requests pile up, compliance becomes a spreadsheet nightmare, and improper access lingers undetected—often until it’s too late.
The Perfect Storm: Why Traditional Identity Governance Fails
The challenges creating this perfect storm are interconnected:
Scale and Complexity
When a single manager must manually review over 1,000 access items each quarter, human limitations become painfully apparent. Users accumulate excessive privileges over time (“entitlement sprawl” or “privilege creep”), creating a tangled web impossible to manage manually.
The Human Element
The Verizon Data Breach Investigations Report found a staggering 82% of breaches involve the “human element”—misused credentials or errors. More concerning, a recent study discovered 99% of cloud identities had excess privileges. Every unnecessary permission is a potential attack vector or security vulnerability.
This broken system creates an unsustainable cycle: overwhelmed managers “approve all” during access reviews, defeating the purpose of governance, while IT teams drown in mundane access tasks instead of focusing on strategic security initiatives.

Enter Artificial Intelligence: The Game-Changer
AI is transforming identity governance and administration from a reactive, labor-intensive exercise into something far more powerful. Let’s explore how intelligent automation is revolutionizing this field.
Finding Needles in the Access Haystack
AI excels at pattern recognition across massive datasets—precisely what’s needed to spot risky outliers. By analyzing peer group behavior, machine learning can flag when someone’s access deviates suspiciously from others in similar roles, identifying potential identity risks before they materialize.
This capability alone transforms governance from backward-looking compliance to proactive risk management and threat prevention.
Real-World Impact: The Numbers Don’t Lie
Organizations implementing AI-powered identity governance and identity security are seeing remarkable results:
- RWE (Energy): Reduced user onboarding from 25 days to less than 3 hours
- ECU Health: Compressed access provisioning from weeks to approximately 4 hours
- PG&E (Utilities): Virtually eliminated “rubber-stamp approvals” by using AI to auto-approve low-risk access while highlighting truly concerning entitlements
One company identified and eliminated over 11,000 hours of excess access rights that would have gone undetected through traditional methods. Another found that 84% of risky access discovered by AI would have been missed entirely by manual reviews and certifications.

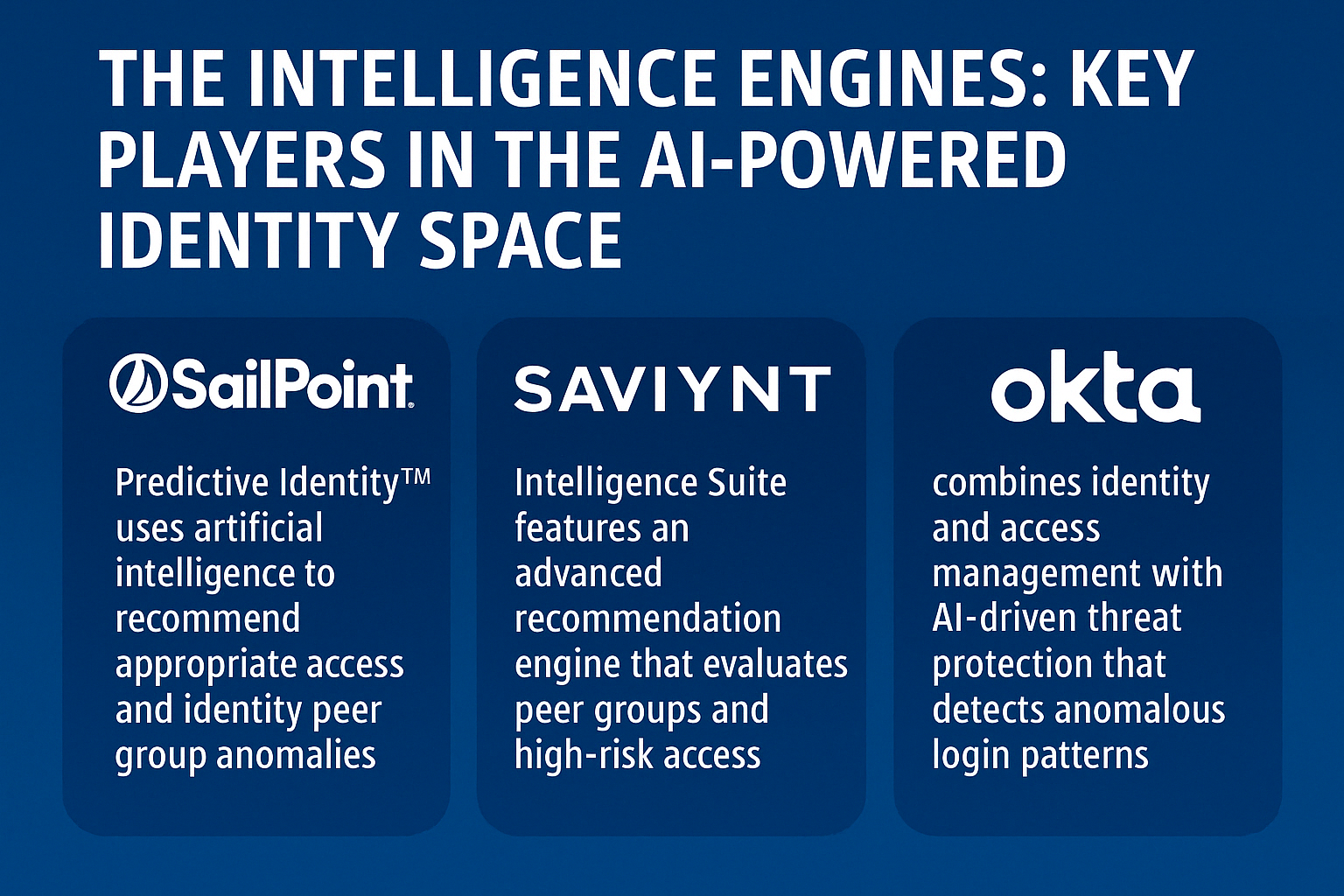
The Intelligence Engines: Key Players in the AI-Powered Identity Space
Several vendors have emerged as leaders in this space:
SailPoint Identity Security Cloud
SailPoint’s Predictive Identity™ uses artificial intelligence to recommend appropriate access, identify peer group anomalies, and auto-discover new access that needs governance. Their identity management platform has been adopted by nearly 46% of Fortune 500 companies.
Saviynt Enterprise Identity Cloud
Saviynt’s Intelligence Suite features an advanced recommendation engine that evaluates peer groups and usage patterns while filtering out high-risk suggestions. Their AI Copilot guides managers through access certification decisions in plain language, reportedly reducing certification fatigue by up to 75%.
Okta Identity Cloud
Okta combines identity and access management with AI-driven threat protection that detects credential attacks by spotting anomalous login patterns. Their Policy Recommender suggests stronger access policies based on insights from across their customer base.
Implementation: A Strategic Journey, Not Just a Technology Deployment
Successfully implementing AI in identity governance requires a thoughtful approach:
- Start with clear objectives – Define specific goals like cutting access request time or reducing unnecessary privileges
- Focus on data quality – AI is only as good as the data it learns from
- Begin with low-hanging fruit – Automate routine processes first to build confidence
- Implement risk-based policies – Configure how AI measures risk and what actions to take
- Involve stakeholders early – Train users and ensure they understand the benefits
The Future Horizon: Where AI and Identity Governance Are Heading
As this technology matures, several exciting trends are emerging:
Continuous Authentication and Zero Trust
Traditional authentication happens at login, but the emerging model leverages AI to continuously validate that a user’s behavior and risk level justify ongoing access—a foundational element of Zero Trust security and advanced access control.
Behavioral Analytics
Beyond static role analysis, advanced behavioral analytics are establishing baselines of “normal” activity for each identity. Deviations can trigger responses ranging from additional verification to access revocation, creating a more dynamic security posture.
But we’ll explore these future identity governance trends in detail another time…
The Bottom Line: Transform or Fall Behind
Identity governance is at a crossroads. Traditional approaches are breaking under the weight of digital transformation, but AI offers a timely solution. The organizations embracing AI for identity governance now are not only solving today’s challenges but building a foundation for adaptive, resilient security for years to come.
The future of identity governance is intelligent, automated, and proactive. The only question is: will your organization be part of it?